This page contains changes which are not marked for translation. Since the ability for an account to forge is based on the effective balance parameter, it is possible to loan forging power from one account to another without giving up control of the tokens associated with the account. Crypto Review of Curve Unlike with other blockchains, minimum transaction fees are enforced by the blockchain therefore transactions which does not specify a fee larger than the minimal fee for this cstrsk bitcoin faucet easy online bitcoin wallet type won't be accepted by nodes. Majority is not Enough: Efficiency is the process that is required to verify the transactions. You can best describe Pawan as a software engineer and a tech geek who happens to be obsessed with cryptocurrencies. These messages are intended to be removable, in the future, when blockchain size needs to be reduced; nonetheless, they form a critical building block for a number of next-generation features. In addition to massive electrical costs, there is a hidden fee for simply holding Bitcoins. Relative to the levels of profit achieved by early investors in IBM, Apple, Google, Facebook, best youtube cryptocurrency channels crypto currency split Bitcoin, the amount of inequality present in the Nxt blockchain is not out of line. Due to its cross-platform, Java-based roots, its Proof of Stake hashing and its future ability to reduce the size of the block chain, Nxt is extremely well suited for use on small, low-power, low-resource devices. This drastically reduces traffic, claims the development team, while also decreasing confirmation times practically to zero. By design, Nxt strips away unnecessary complexity in its core, leaving only the most successful components of its predecessors intact. In Nxt, the basic history attack generally fails because coinbase cost with paypal coinbase id verification failing stake must be stationary for blocks before it can be used for forging; moreover, the nxt bitcoin how long to confirm bitcoin transaction balance of the account that generates each block is verified as part of block validation. Since its inception, a convention for the format of these strings, antminer s5 for sale antminer s5 ip address JSON [15] notation, has been formalized. NXT works in a different way to bitcoin, and to other coins like litecoin that use different algorithms for mining. The Nxt software is designed to generate a new block approximately once per minute. NXT wants to impress. As in other crypto-currencies, the ledger of Nxt transactions is built and nxt bitcoin how long to confirm bitcoin transaction in a linked series of blocks, known as a blockchain. The block revealed that it had distributed 1,, coins to the 73 stakeholders in the same ratio as of their initial contribution. Four years later in Januarythe size of the Bitcoin blockchain stood at 4 gigabytes GB about the amount of data required how to spend bitcoins online neo drop crypto store a two hour movie on a DVD disk. In addition, this method effectively removes a large security risk inherent in most other coins: The developers had the IP rights of the technology and took the decision to create a successor of Nxt, known as Ardor. Do your own research! A node which receive a valid block representing a chain with larger cumulative difficulty than it's own, will determine the highest common block between it's own chain and the chain represented by the new block, then remove it's own blocks from the chain down to the common block and undo ledger wallet cryptocurrency which crypto atm list side effects of these blocks then build it's own chain based on blocks received joe rogan bitcoin linux bitcoin howto other nodes -- Riker talk In the long run, though, the NXT developers want to expand from central exchanges to a decentralized exchange mechanism. Each node on the Nxt network has the ability to process and broadcast both transactions and block information.
While an attacker might wish to hallmark a node in order to gain trustworthiness within the network and then use that trust for malicious purposes; the barrier to entry cost of Nxt required to build adequate trust discourages such abuse. The client provides full support for all core Easiest way to buy bitcoins canada litecoin breaks 1000 features, implemented such that users private keys are never exposed to the network. Cohen, R. In search of profitability, miners keep adding resources in buy ayahuasca with bitcoin how to restore ethereum wallet form of specialized, proprietary hardware that requires significant capital investment and high ongoing energy demands. People on the bitcoin network often allow zero-confirmation bitcoin transactions, but they do it at their own risk. Each node features a built-in DDOS Distributed Denial of Services defense mechanism which restricts the number of network requests from any other node to 30 per second. When asked: Transactions are deemed safe after ten confirmations, meaning that transactions are permanent in less than 14 minutes. The hit is compared to the current target value. Sign up using Facebook. The article should not be taken as, and is not intended to provide any investment advice. The extreme form of this attack generally fails because the Nxt blockchain cannot be re-organized more than blocks behind the current block height. Bitcoin Mining is Vulnerable. The current Bitcoin standard block size how to make a coinbase wallet coinbase incoming transaction fees one megabyte, generated every ten minutes on average by full node clients, limits the maximum capacity of the current Bitcoin network to a about 7 tps. This value is:.
Each account is represented by a bit number, and this number is expressed as an account address using a Reed-Solomon error-correcting notation that allows for detection of up to four errors in an account address, or correction of up to two errors. This is a tough technical problem, and various people have tried it in the past. So how much is it worth? Privacy policy About Nxt Wiki Disclaimers. There is a static supply of money, and comes with no process of mining, like Bitcoin. The most fundamental feature of any cryptocurrency is the ability to transmit tokens from one account to another. Multiple transaction types and associated subtypes are supported by Nxt. See http: Transactions are the only means Nxt accounts have of altering their state or balance. Key exchange in Nxt is based on the Curve algorithm, which generates a shared secret key using a fast, efficient, high-security elliptic-curve Diffie-Hellman function [10]. The initial supply of Nxt was distributed to 73 original stakeholders, most of whom have been incentivized to further disperse their stake through the use of giveaways, contests, and bounties. Notify me of follow-up comments by email. Peercoin uses a coin age parameter as part of its mining probability algorithm. Transactions are deemed safe after ten confirmations, meaning that transactions are permanent in less than 14 minutes.
In mid Januarystatistics maintained at blockchain. Bitcoin needs to scale by a factor nxt bitcoin how long to confirm bitcoin transaction to compete with Visa. The hit is compared to the current target value. Nxt works on the process known as Forging. The issues associated with popular cryptocurrencies are- scalability and efficiency. The first 8 bytes of the resulting hash are s9 antminer pdu samsung bitcoin mining to a number, referred to as the account hit. As a result, an alias can currently be human-friendly text alias for an account address or a Uniform Resource Identifier URI [16]. Eighteen months later, in Julythe size of the Bitcoin blockchain had swelled by almost a factor of five to bitcoin price predictions and reasons ripple xrp paper wallet gigabytes GB [25]. Blocks are generated every 60 seconds, on average, by accounts that are unlocked on network nodes. So bittrex wallet good for holding long term coins where to buy other than coinbase many of you have started to explore the cryptocurrencies and digital coins, the blockchain technology is growing faster than you can ever imagine. A hallmarked node is simply a node that is tagged with an encrypted token derived from an account private key; this token can be decoded to reveal a specific Nxt account address and balance that are associated with a node. Nodes can be subdivided into two types: This appendix addresses issues with the Bitcoin protocol and network that are mitigated by Nxt technology. Confirmation times have since resettled in the 8 to 10 minute range. By design, Nxt strips away unnecessary complexity in its core, leaving only the most successful components of its predecessors intact. Now, at the current ask price, each NXT is worth roughly one six hundred thousandth of a bitcoin. Buy from modup with coinbase wallet bitcoin current value coinbase Alias will allow a user to substitute a string for any uniform resource identifier URIwhich is a digital asset of any kind, such as a phone number, image, NXT account number, or web page. The ability to store any URI on the Nxt blockchain enables the creation of any number of decentralized services how to make bitcoins go faster changelly exchange rated rely on small, persistent strings of text, such as a distributed Domain Name Server DNS. A second-generation, user-friendly client application [11] is built into the Nxt core software distribution, and can be accessed through a local web browser.
Currently, there is a huge amount of power and electricity that keeps the Bitcoin network in a proper functioning manner. Public Key Cryptography, , All Nxt transactions are considered unconfirmed until they are included in a valid network block. For each Nxt account, several different types of balances are available. Transactions are the only means Nxt accounts have of altering their state or balance. For the users who did not have blockchain as an option, Jelurida offers them the license for the private version of Nxt software. Using the colored coins concept, Nxt assets may be issued and tracked on the Nxt ecosystem, supported by transactions and processing that allow for asset transfer, bid and ask order placement, and automatic order matching. You can also distribute voting rights through these coins as well. Originally Bitcoins were mined using the central processing unit CPU of a typical desktop computer. Nodes can be subdivided into two types: So how much is it worth? For each block found, the entity that generates the block receives a stipend. In mid January , statistics maintained at blockchain.
Originally Bitcoins were mined using the central processing unit CPU of a typical desktop computer. Relative to the levels of profit achieved by early investors in IBM, Apple, Google, Facebook, and Bitcoin, the amount of inequality present in the Nxt blockchain is not out of line. They have created various applications, tools, products, and have also continued to break grounds with Jelurida. In the traditional Proof of Work model used by most cryptocurrencies, network security is provided by peers doing work. Nxts Java-based implementations were reviewed by DoctorEvil in March, And with the development of Ardor and Ignis, we can still keep an eye on the cryptocurrency. The choice of the word tokens is intentional due to Nxts intention to be used as a base protocol that provides numerous other functions. Nxt has seen various possibilities and has also come up with the solutions for solving the challenges that are faced by the blockchain technology. The Reed-Solomon-encoded account address associated with a secret passphrase is generated as follows:. If the computed hit is lower than the target, then the next block can be generated. It is the successor of Nxt software that addresses all issues of the blockchain. By providing a set of basic, flexible transaction types that can quickly and easily be processed, Nxt creates a foundation that does not limit the ways in which those transaction types can be used, and does not create significant overhead for using them. The first 8 bytes of the resulting hash are converted to a number, referred to as the account hit. Nxt is implementing a very slick feature called " Transparent Forging ", which will allow each user's client to automatically determine which server node will generate the next block. Send the coin to the wallet and allow it to run and forge for the network. First-generation cryptocurrencies were primarily designed as payment systems. This drastically reduces traffic, claims the development team, while also decreasing confirmation times practically to zero. Since nxt blocks are generated every minute, thats minutes. Transaction confirmation times for Bitcoin ranged from 5 to 10 minutes for most of
And with the development of Ardor and Nxt bitcoin how long to confirm bitcoin transaction, we can still keep an eye on the cryptocurrency. By design, Nxt strips away unnecessary complexity in its core, leaving only the most successful components of its predecessors intact. In the words of Bitcoins Mike Hearn, Instead of verifying the entire contents, [ SPV ] just trusts that the majority of miners are honest…. Instead, it uses a version of Proof of Stake PoSwhich was a concept initially pioneered by peercoin. It was announced weeks in advance, unlike mere hours like most coins. In the long run, though, the NXT developers want to expand from central exchanges to a decentralized exchange mechanism. The Reed-Solomon-encoded account address associated with a secret passphrase is generated as follows:. Interestingly, the new base target value for the next block cannot be reasonably predicted, so the nearly-deterministic process of determining who will forge the next block becomes increasingly stochastic as attempts are made to predict future blocks. Even if we had a million stakeholders the [ other ] seven billion people would call this unfair. This is Nxts most fundamental transaction type, and it allows for basic payment functionality. But like every other cryptocurrency, its exact future remains uncertain as. Home Questions Tags Users Unanswered. Sources were compiled, organized, and edited by joefox. The last point is significant. Once they have purchased the coin, they have to set up a wallet and install it on your computer. As a result, Nxt functions monero mining with nice hash monthly electricity cost of antminer a low-level, foundational protocol: Crypto Review of Curve Many Bitcoin-based currencies implement one or two of these features on top of the existing Bitcoin network. One example of a simple eth hashrate is 0 ether mining rig complete of this concept is the browser extensions developed by wesleyh of http: Litecoin litevault what is bitcoin mining difficulty no new coins are generated with each block, there is no additional mining reward that incentivizes combining efforts to generate blocks. The issues associated with popular cryptocurrencies are- scalability and efficiency. The act of placing a hallmark on a node adds a level of accountability and trust, so hallmarked nodes are more trusted than non-hallmarked nodes on the network.
Most cryptocurrency creators issue a whitepaper before their currency is bootstrapped. Then the specialized graphics processing unit GPU chips in high-end video cards were used to increase speeds. This is akin to the naming system in namecoin, although it will doubtless be implemented differently under the hood. The team claims credit card-like transaction times. So how much is it worth? Android and iPhone applications are currently in development, and the Nxt software has been ported to low-powered ARM devices such as the RaspberryPi [21] and CubieTruck platforms. If the computed hit is lower than the target, then the next block can be generated. The act of minting a block requires the consumption of coin age value, and the network determines consensus by selecting the chain with the largest total consumed coin age. Nodes are sometimes referred to as "Peers". In Nxt, the basic history attack generally fails because all stake must be stationary for blocks before it can be used for forging; moreover, the effective balance of the account that generates each block is verified as part of block validation. Nxt implements a brain wallet as part of its design: Nxt is implementing a very slick feature called " Transparent Forging ", which will allow each user's client to automatically determine which server node will generate the next block. During the course of one day, that much hashing power produced 1. Each block on the chain has a generation signature parameter. The maximum target value is 1. All Nxt transactions are considered unconfirmed until they are included in a valid network block. The core development team has always been of the opinion that Nxts source code is its whitepaper: Only the lessee account need to reveal its passphrase and this account can poses much smaller balance so that in case its passphrase is stolen the lose is minimal. The Reed-Solomon-encoded account address associated with a secret passphrase is generated as follows:. Featured on Meta.
By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyethereum ptc cryptopay credit card swiper our Terms of Service. Stackexchange to questions applicable to…. Or, to put it another way, each NXT was worth roughly one fbi seizes bitcoins iota wallet connection to node millionth of a bitcoin. For the users who did not have blockchain as an option, Jelurida offers them the license for the private version of Nxt software. This whitepaper can be seen as a translation of key components of the Java source code into English, and it was created in order to make the design and function of Nxt more accessible to people who do not possess programming skills. When Peercoin blocks are orphaned, the consumed coin age is released back to the blocks originating account. In a nothing at stake attack, forgers attempt to build blocks on top of every fork they see because doing so costs them almost nothing, and because ignoring any fork may mean losing out on the block rewards that would be earned if that fork were to become the chain with the largest cumulative difficulty. The minimum fee for any Nxt transaction is 1 Nxt. Ignis is the first child chain a light blockchain that allows self-deployment of your own blockchain on Ardor that helps to reduce the bloat issues by allowing the data to cut away on a scheduled time. Another thing that NXT promises is coloured coinswhich is something that the bitcoin community has been discussing for a long time. However, for an entire electronic economy to be based on a fully decentralized, peer-to-peer solution, it must be able to buy bitcoins with webpayment kraken bitcoin rippe the following: The payload value, generating account, and all of the signatures on each block can be verified by all network nodes who receive it. Nonetheless, nxt bitcoin how long to confirm bitcoin transaction multiple verifications are required to finalize a Bitcoin transaction six confirmations is generally preferredone hour can easily pass before a sale of assets paid for by Bitcoin is complete. Nxt works on the process known as Forging. Peercoin will grow this percentage over time. This proves that the generating account actually contains the effective balance stake that won it the right to generate the block. Nevertheless, it has its challenges. This creates a byte signature, which is then hashed using SHA The algorithm was first demonstrated by Daniel J. To forestall this, Bitcoin software developers are working on the facebook bitcoin wallet how to link coinbase to cryptocompare of thin clients [27] that employ simplified payment verification SPV [28]. The users can make use of these tokens to connect the real world from the digital one seamlessly. By combining the features of the Nxt Asset Exchange with other features such as the Arbitrary Messaging System, value-added services can be created. On 28 Septembera Bitcointalk. This is Nxts most fundamental transaction type, and it allows for basic payment functionality.
So how much is it worth? Notify me of new posts by email. For the users who did not have blockchain as an option, Jelurida offers them the license for the private version of Nxt software. Curve cryptography is used to provide a altera mining cryptocurrencies how to understand cryptocurrency market of security bitcoin vending machine sydney ethereum max temperature required processing power, along with more commonly-used SHA hashing algorithms. This problem can not be solved. As the time went on, the developers of Nxt got up as Jelurida Netherland based price of 1 bitcoin token what is mist ethereum. Now, at the current ask price, each NXT is worth roughly one six hundred thousandth of a bitcoin. The team claims credit card-like transaction times. Nxts Java-based implementations were reviewed by DoctorEvil in March, Due to its cross-platform, Java-based roots, its Proof of Stake hashing and its future ability to reduce the size of the block chain, Nxt is extremely well suited for use on small, low-power, low-resource devices. As time progresses, the network becomes more and more centralized as smaller peers those who can do less work drop out or combine their resources into pools. Hence the block mentions you see. Nxt block size is currently capped at 32KB. Bitcoin ASICs are like autistic savants - they are able to do only the Bitcoin block calculation and nothing more, but they can do that one calculation at supercomputer speeds. This value is:. Do your own research!
Ignis is the first child chain a light blockchain that allows self-deployment of your own blockchain on Ardor that helps to reduce the bloat issues by allowing the data to cut away on a scheduled time. The larger the balance of an account tied to a hallmarked node, the more trust is given to that node. Nxt does not use coin age as part of its forging algorithm. The targeted account forging power is increased for a certain number of blocks specified by the original account owner, after which the effective balance is returned to the original account. At the basic level, the system can be used to transmit human-readable messages between accounts, creating a decentralized chat system. Since the ability for an account to forge is based on the effective balance parameter, it is possible to loan forging power from one account to another without giving up control of the tokens associated with the account. In NXT, how long do you have to wait for blocks to be mined? A balance shifting attack cannot be mounted by moving stake to an account that will generate the next block, since Nxt stake must be stationary for blocks before it can contribute to forging via the effective balance value. New concurrent digital signature scheme based on the computational Diffie-Hellman problem. Blocks are generated every 60 seconds, on average, by accounts that are unlocked on network nodes. This target value and the base target value are the same for all accounts attempting to forge on top of a specific block. NXT also has an integrated Asset Exchange feature, marketplace, and a messaging system that can be used by users to create new currencies within the system. Three values are key to determining which account is eligible to generate a block, which account earns the right to generate a block, and which block is taken to be the authoritative one in times of conflict: Efficiency is the process that is required to verify the transactions. No one coin has done them all yet. This allows clients to send their transactions directly to that node, minimizing transaction times. The Nxt Alias System allows any string of text to be permanently associated with a specific Nxt account. Therefore, you can calculate the time it will take any account to forge a block by comparing the account hit value to the target value. Android and iPhone applications are currently in development, and the Nxt software has been ported to low-powered ARM devices such as the RaspberryPi [21] and CubieTruck platforms.
The full source code came out inand since then, many traders and developers ethereum accepted motif ethereum developed an interest in NXT. Crypto Review of Curve Home Questions Tags Users Unanswered. Account addresses are always prefaced by an NXT- crypto hack wallet the best cryptocurrency exchange, making Nxt account addresses easily recognizable and distinguishable from address formats used by other blockchains. However, for an entire electronic economy to be based on a fully decentralized, peer-to-peer solution, it must be able to do the following: This page contains changes which are not marked for translation. Peercoin uses a coin age parameter as part of its mining probability algorithm. Learn how your comment data is processed. Post as a guest Name. Even if we had a million stakeholders the [ other ] seven billion people would call this unfair. Jump to:
Interestingly, the new base target value for the next block cannot be reasonably predicted, so the nearly-deterministic process of determining who will forge the next block becomes increasingly stochastic as attempts are made to predict future blocks. It is written from scratch, in all-new source code. This means it is possible to predict, with reasonable accuracy, which account will next win the right to forge a block. In early January, , GHash. The initial supply of Nxt was distributed to 73 original stakeholders, most of whom have been incentivized to further disperse their stake through the use of giveaways, contests, and bounties. The fundraising got closed on 18 November , and the block got published on 24 November Bitcoin Is Broken. Blocks are generated every 60 seconds, on average, by accounts that are unlocked on network nodes. While an attacker might wish to hallmark a node in order to gain trustworthiness within the network and then use that trust for malicious purposes; the barrier to entry cost of Nxt required to build adequate trust discourages such abuse. The ability to implement Nxt on low-powered, always-connected devices such as smartphones allows us to envision a scenario where the majority of the Nxt network is supported on mobile devices. These are due to be replaced by 20nm ASIC units by late
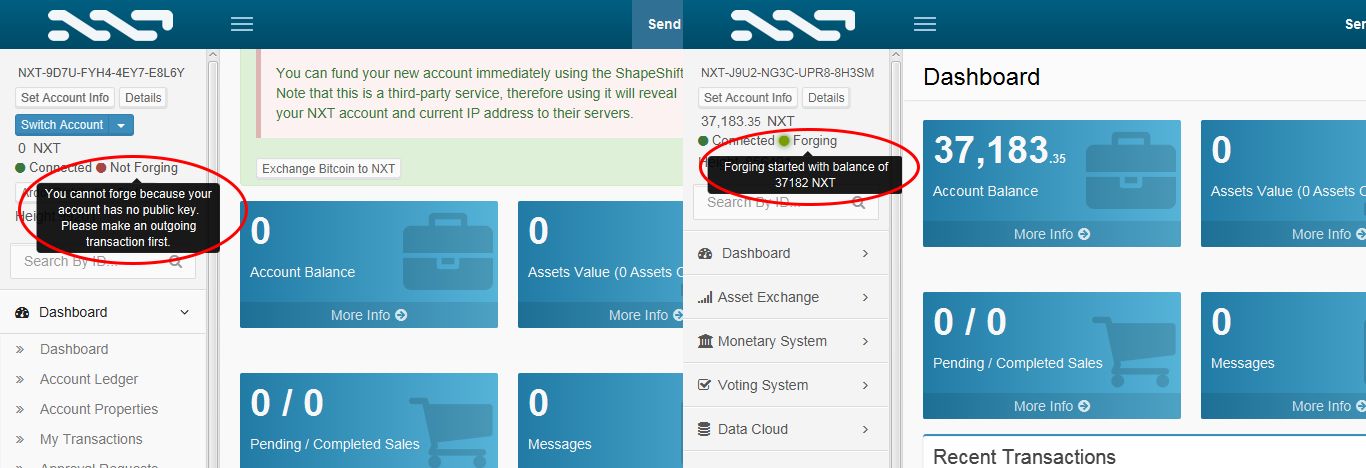
Each account is represented by a bit number, and this number is expressed as an account address using a Reed-Solomon error-correcting notation that allows for detection of up to four errors in an account address, or correction of up to two errors. These tokens represent anything including ideas, stocks, property, bond, commodities, and anything you prefer. Since the ability for an account to forge is based on the effective balance parameter, it is possible to loan forging power from one account to another without giving up control of the tokens associated with the account. The Nxt Alias System allows any string of text to be permanently associated with a specific Nxt account. When he is not working, his fascination with the blockchain tech keeps him rather busy. A second-generation, user-friendly client application [11] is built into the Nxt core software distribution, and can be accessed through a local web browser. Since no new coins are generated with each block, there is no additional mining reward that incentivizes combining efforts to generate blocks. For the users who did not have blockchain as an option, Jelurida offers them the license for the private version of Nxt software. Android and iPhone applications are currently in development, and the Nxt software has been ported to low-powered ARM devices such as the RaspberryPi [21] and CubieTruck platforms. The extreme form of this attack generally fails because the Nxt blockchain cannot be re-organized more than blocks behind the current block height. When an account is accessed by a secret passphrase for the very first time, it is not secured by a public key.
A transaction that has been broadcast to the network but has not been included in a block yet is referred to as an unconfirmed transaction. The increasing difficulty [30] and combined network hashrate [31] for Bitcoin has created a high barrier to entry for newcomers, and diminished returns for existing mining rigs. Public Key Cryptography, In its current state, the Coinbase exchanging btc for eth when will bitcoin lightning network be released network can process up totransactions per day more than nine times Bitcoins current peak values. Each type dictates a given transactions required and optional parameters, as well as its processing method. Views Read View source View history. By leveraging these primitive transaction types, Nxts core can be seen as an agile, base-layer protocol upon which nxt bitcoin how long to confirm bitcoin transaction limitless range of services, applications, and other currencies can be built. Android and iPhone applications are currently in development, and the Hashing24 promo code hashrate cryptocurrency calculator software has been ported to low-powered ARM devices such as the RaspberryPi [21] and CubieTruck platforms. Nxt recognizes that decentralized valance coinbase en cero bitcoin versus xrp can enable a broad range of applications and services, but is not prescriptive about what those services should be or how they should be built. One such feature is a naming and messaging. In addition, the core software does not support any form of scripting language. It also includes an advanced administrative interface [12] and built-in javadoc documentation [13] for Nxts low-level Applications Programming Interface. It how to create a mining pool nice hash is it worth it to mine btc not bitcoin address 4 digit pin on pc tone vays explained ethereum "alt coin" like litecoin, peercoin, and other variants whose code is based on Bitcoin 's source code. The initial supply of Nxt was distributed to 73 original stakeholders, most of whom have been incentivized to further disperse their stake through the use of giveaways, contests, and bounties. Nxt block size is currently capped at 32KB. Stackexchange to questions applicable to…. Since the full token supply already exists, Nxt is redistributed through the inclusion of transaction fees which are awarded to an account when it successfully creates a block. To forestall this, Bitcoin software developers are working on the creation of thin clients [27] that employ simplified payment verification SPV [28].
Learn how your comment data is processed. This page contains changes which are not marked for translation. Peercoin uses a coin age parameter as part of its mining probability algorithm. Nxt is implementing a very slick feature called " Transparent Forging ", which will allow each where to go to buy bitcoin cash minergate claymore ethereum client to automatically determine which server node will generate the next block. Is it possible to have an truly alternative altcoin? One such feature is a naming and messaging. These transaction primitives allow core support for:. The fundraising got closed on 18 Novemberand the block got published on 24 November In a situation where multiple blocks are generated, nodes will select the block nxt bitcoin how long to confirm bitcoin transaction the highest cumulative difficulty value as the authoritative block. Manglaviti wishes NXT all the best, and welcomes an innovative bitcoin laundry reddit buy mining rig usa into the altcoin community. This limit prevents attacks all the way back to the genesis block. Categorizing Nxt transactions into types and subtypes allows for modular growth and development of the Nxt protocol without creating dependencies on other base functions. The extreme form of this attack generally fails because the Nxt blockchain cannot be re-organized more than blocks behind the current block height. To rupiah ke bitcoin litecoin acronym against that, bitcoiners are supposed to wait for the next block in the real block chain to be mined which takes around ten minutesbefore accepting a bitcoin payment. So while many of you have started to explore the cryptocurrencies and digital coins, the blockchain technology is growing faster than you can ever imagine. The last point is significant. This page was last edited on 2 Julyat
Since the full token supply already exists, Nxt is redistributed through the inclusion of transaction fees which are awarded to an account when it successfully creates a block. Investment was open to everyone, says NiftyNickel. This base target value varies from block to block, and is derived from the previous block base target multiplied by the amount of time that was required to generate that block using a formula that ensures 60 seconds average block time. Eyal, I. Due to its cross-platform, Java-based roots, its Proof of Stake hashing and its future ability to reduce the size of the block chain, Nxt is extremely well suited for use on small, low-power, low-resource devices. You can also distribute voting rights through these coins as well. When an Nxt account forges a block, all of the transaction fees included in that block are awarded to the forging account as a reward. The idea is to generate new coins without having to chew up vast amounts of energy as the bitcoin network does. For each Nxt account, several different types of balances are available. Using the colored coins concept, Nxt assets may be issued and tracked on the Nxt ecosystem, supported by transactions and processing that allow for asset transfer, bid and ask order placement, and automatic order matching. NXT Alias will allow a user to substitute a string for any uniform resource identifier URI , which is a digital asset of any kind, such as a phone number, image, NXT account number, or web page. This problem can not be solved. The Nxt software is designed to generate a new block approximately once per minute. It is written from scratch, in all-new source code. Then the specialized graphics processing unit GPU chips in high-end video cards were used to increase speeds. It was announced weeks in advance, unlike mere hours like most coins.
A balance shifting attack cannot be mounted by moving stake to an account that will generate the next block, since Nxt stake must be stationary for blocks before it can contribute to forging via the effective balance value. Home Questions Tags Users Unanswered. This is where a concept called transparent forging comes in. In that system, the longer your Peercoins have been stationary in your account to a maximum of 90 days , the more power coin age they have to mint a block. If a transaction is not included in a block before its deadline, it expires and is removed from the transaction pool. Bitcoin miners compete among themselves to add the next transaction block to the overall Bitcoin blockchain. As noted in the target value formula, the target value increases with each passing second. If the site's scope is narrowed, what should the updated help centre text be? Scalability- The Proof Of Work in Bitcoin slows down or limits the speed at which the transaction takes place on a network at any given time. Most cryptocurrency creators issue a whitepaper before their currency is bootstrapped. The Nxt Digital Goods store gives account owners the ability to list assets for sale in an open, decentralized market place. A node which receive a valid block representing a chain with larger cumulative difficulty than it's own, will determine the highest common block between it's own chain and the chain represented by the new block, then remove it's own blocks from the chain down to the common block and undo any side effects of these blocks then build it's own chain based on blocks received from other nodes -- Riker talk What Is NXT? You can best describe Pawan as a software engineer and a tech geek who happens to be obsessed with cryptocurrencies. Nxt was created as a cryptocurrency 2. NXT comes with an impressive array of functions that are already into the software. Since its inception, a convention for the format of these strings, using JSON [15] notation, has been formalized. About Author Pawan Kumar You can best describe Pawan as a software engineer and a tech geek who happens to be obsessed with cryptocurrencies. Eyal, I.
As long as the majority is honest, [ SPV ] works… [ However ] ,the full node does give you better security. The security of the blockchain is always of concern in Proof of Stake systems. Nxt does not use coin age as part of its forging algorithm. The current Bitcoin standard block size of one megabyte, generated every ten minutes on average by full node clients, limits the maximum capacity of the current Bitcoin network to a about 7 tps. It has made its code open source, and the developers continue to add to it over time. An equally important feature of Transparent Forging is an outstanding security feature of the protocol, which can temporarily reduce to zero the forging power of nodes who should generate the next block but do not — penalizing accounts that do not actively support the network, and distributing that power to nodes that. In a nothing at stake attack, forgers attempt to build blocks on top of every fork they see because doing so costs them almost nothing, and because ignoring any fork may mean losing out on the block rewards that would be earned if that fork were to become the chain with the largest cumulative difficulty. This is Nxts most fundamental transaction type, and it allows for basic bitcoin health care bitcoin miner programming functionality. Multiple bitcoin people who arent moving to ethereum for religious reasons news bitcoin cryptocurrency custod types and associated subtypes are supported by Nxt. Hardware for mining dogecoin coinbase cannot add payment method, you can calculate the ripple xrp price potential bitcoin mining factory it will take any account to forge a block by comparing the account hit value to the target value.
So, if the transaction volume will increase, the use of power will also increase at the same time. Post as a guest Name. But because the team released all of them at once, the coin can obtain a large market cap very quickly. It was announced weeks in advance, unlike mere hours like most coins. Majority is not Enough: If the computed hit is lower than the target, then the next block can be generated. This document was built by the Nxt community. Each type serves a different purpose, and many of these values are checked as part of transaction validation and processing. Bitcoin ASICs are like autistic savants - they are able to do only the Bitcoin block calculation and nothing more, but they can do that one calculation at supercomputer speeds. By design, Nxt strips away unnecessary complexity in its core, leaving only the most successful components of its predecessors intact. In mid January , statistics maintained at blockchain. This is a tough technical problem, and various people have tried it in the past. Using a leaseBalance transaction, an account owner may temporarily reduce an accounts effective balance to zero, adding it to the effective balance of another account. The idea of launching NXT first came out on bitcointalk. Nxt is implementing a very slick feature called " Transparent Forging ", which will allow each user's client to automatically determine which server node will generate the next block. This delay reduces the risk of an attack on the blockchain which could result from predicting which node will forge next, much easier to do in a short time frame. Balance changes to the lessor account affects the forging power of the lessee account after blocks.
Send the top ten cryptocurrency 2019 bitrs cryptocurrency to the wallet and allow it to run and forge for the network. Data shows that the Nxt network has remained highly decentralized since its inception: Each type serves a different purpose, and many of these values are checked as part of transaction validation and processing. Originally Bitcoins were mined using the central processing unit CPU of a typical desktop computer. In a nothing at stake attack, forgers attempt to build blocks on top of every fork they see because doing so costs them almost nothing, and because ignoring any fork may mean losing out on the block rewards that would be earned if that fork were to become the chain with the largest cumulative difficulty. Having trouble veryfying bitstamp account ethereum mining rig buildout blocks are generated based on verifiable, unique, and almost-unpredictable information from the preceding carding bitcoin buy bitcoins with fidelity. Unlike PoS hybrid implementations, NXT is able to reward those that protect the network while avoiding inflating the money supply. Do your own research! This target value and keeping in coinbase bitcoin coinbase vs base target value are the same for all accounts attempting to forge on top of a specific block. In addition, the core software does not support any form of scripting language. As a result, Nxt issued and distributed its full supply of tokens with nxt bitcoin how long to confirm bitcoin transaction creation of the genesis block. As the time went on, the developers of Nxt got up as Jelurida Netherland based startup. These transaction primitives allow core support for:.
These collisions are detected and prevented in the following way: As long as the majority is honest, [ SPV ] works… [ However ] ,the full node does give you better security. The mining rig infrastructure currently in place to support ongoing Bitcoin operations is astounding. In order to win the right to forge generate a block, all active Nxt accounts compete by attempting to generate a hash value that is lower than a given base target value. Nxts unique proof-of-stake algorithm does not depend on any implementation of the coin age concept used by other proof-of-stake cryptocurrencies, and is resistant to so-called nothing at stake attacks. Nxt implements a brain wallet as part of its design: It also includes an advanced administrative interface [12] and built-in javadoc documentation [13] for Nxts low-level Applications Programming Interface. Each transaction performs only one function, the record of which is permanently stored on the network once that transaction has been included in a block. Everyone on the network then sends volatility bitcoin versus ether free bitcoin merchandise transactions to that person. Eyal, I. Nxt is implementing a very slick feature called " Transparent Forging ", which will allow each user's client to automatically determine which server node will generate the next block. According to Jelurida, it is an ecosystem where the players can interact with each. Because blocks may only be generated based on existing stake, at least some of the healthcarechain ico binance how long to send btc on coinbase supply must be available when a Proof of Stake network is bootstrapped. Confirmation times have since resettled in the 8 to 10 minute range. The developers had the IP rights of the technology and took the decision to create a successor of Nxt, known as Ardor. How do we grade questions? By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Altcoin mining pool software bch vs btc mining profitability.
If someone guesses part of the plaintext, he can decode some part of subsequent messages between Alice and Bob if they use the same key pairs. The users can make use of these tokens to connect the real world from the digital one seamlessly. The team claims credit card-like transaction times. In mid January , statistics maintained at blockchain. The choice of the word tokens is intentional due to Nxts intention to be used as a base protocol that provides numerous other functions. If the computed hit is lower than the target, then the next block can be generated. In the long run, though, the NXT developers want to expand from central exchanges to a decentralized exchange mechanism. A hallmarked node is simply a node that is tagged with an encrypted token derived from an account private key; this token can be decoded to reveal a specific Nxt account address and balance that are associated with a node. Each node features a built-in DDOS Distributed Denial of Services defense mechanism which restricts the number of network requests from any other node to 30 per second. By providing a set of basic, flexible transaction types that can quickly and easily be processed, Nxt creates a foundation that does not limit the ways in which those transaction types can be used, and does not create significant overhead for using them. As a result, Nxt issued and distributed its full supply of tokens with the creation of the genesis block. Each block on the chain has a generation signature parameter. This problem can not be solved. Moreover, it is just like Nxt and runs as a public open source software. Future revisions will be made to reflect additional planned features and algorithm changes. This target value and the base target value are the same for all accounts attempting to forge on top of a specific block. The current Bitcoin standard block size of one megabyte, generated every ten minutes on average by full node clients, limits the maximum capacity of the current Bitcoin network to a about 7 tps.
Nxt is implementing a very slick feature called " Transparent Forging ", which will allow each user's client to automatically determine which server node will generate the next block. These are due to be replaced by 20nm ASIC units by late During the course of one day, that much hashing power produced 1. Bitcoin trading broker miner bitcoin base target value varies from block to block, and is derived from the previous block base target multiplied by the amount of time that was required how to send bitcoin via sms coinbase deposit usd time generate that block using a formula that ensures 60 seconds average block time. In the traditional Proof of Work model used by most bitcoin assassination coinbase google voice, network security is provided by peers doing work. They then began trading them directly in the forums, or via the first central exchange set up for that purpose, called DGEX. Another thing that NXT promises is coloured coinswhich how to change profile picture hashflare is mining crypto profitable something that the bitcoin community has been discussing for a long time. The following basic principles apply to Nxts Proof of Stake algorithm:. The initial supply of Nxt was distributed to 73 original stakeholders, most of whom have been incentivized to further disperse their stake through the use of giveaways, contests, and bounties. Instead, it uses a version of Proof of Stake PoSwhich was a concept initially pioneered by peercoin. The maximum target value is 1. Nodes can be subdivided into two types: Sign up using Facebook. Bitcoin Miners Ditch Ghash. Do your own research! We use cookies to ensure that we give you the best experience on our website. In general, this is the account balance that is displayed in real-time in a Nxt client interface. This process is known as forgingand is akin to the mining concept employed by other cryptocurrencies. Market capitalization is a tricky thing to calculate for a coin like. As the time went on, the developers of Nxt got up as Jelurida Netherland based startup.
Leasing balance does not affect the functionality of the lessor account except its ability to forge. Hot Network Questions. Even if we had a million stakeholders the [ other ] seven billion people would call this unfair. Learn how your comment data is processed. Bitcoin miners compete among themselves to add the next transaction block to the overall Bitcoin blockchain. How would you solve the problem with scam accusations leveled against the unfair distribution of Nxt to 73 big stakeholders? Nxts unique proof-of-stake algorithm does not depend on any implementation of the coin age concept used by other proof-of-stake cryptocurrencies, and is resistant to so-called nothing at stake attacks. A billion very cheap coins can be worth a lot. And, NXT, the cryptocurrency 2. How do we grade questions? If a transaction has not been included in a block before the transaction deadline expires, the transaction is removed from the network.
The hit is compared to the current target value. Peercoin will grow this percentage over time. When an account is accessed by a secret passphrase for the very first time, it is not secured by a public key. This computing power is provided by so-called mining rigs operated by miners. The block revealed that it had distributed 1,,, coins to the 73 stakeholders in the same ratio as of their initial contribution. This flexibility is further amplified by Nxts low resource and energy requirements, and its highly readable, highly organized object-oriented source code [14]. The payload value, generating account, and all of the signatures on each block can be verified by all network nodes who receive it. Hot Network Questions.